News 7/19/17
Top News
New CDC Director Brenda Fitzgerald, MD comes to Washington, DC from Atlanta, where she served as the commissioner of the Georgia Dept. of Public Health and state health officer from 2011 to 2017. I have heard her speak many times at metro area health IT events, and have always been impressed by her dedication to helping students become interested in various healthcare career paths. She was also part of a very compelling presentation at Health Connect South several years ago that focused on Atlanta’s role as ground zero for Ebola patients.
Fitzgerald takes over from Interim Director Anne Schuchat, MD who began filling in after President Obama appointee Tom Frieden, MD left the position in January.
HIStalk Practice Musings

Reading: The Barefoot Queen by Spanish author Ildefonso Falcones. I’m a sucker for historical fiction, especially the kind that takes 1,000-plus pages to tell the story of one family over several generations. The stories of Falcones, which include the Ken Follett-esque Cathedral of the Sea, do just that.
When it comes to reading, I typically curl up with a good book in the same place at the same time each day – a ritual this Quartz article claims is one that forms a “strange, new relationship … between [the reader], the voice of the book, and the room. Your ritual creates a singular association between the book and a quiet, private place, which in turn gives your relationship a new dimension.” I’ve never looked at my bedtime reading ritual quite in that way, but I will say it’s usually the calmest, most comfortable part of my day.
Webinars
None scheduled soon. Previous webinars are on our YouTube channel. Contact Lorre for information on webinar services.
Announcements and Implementations

The Carolina Center for Occupational Health implements PrognoCIS EHR software from Bizmatics as part of its transition away from paper documents. The center, which works with hundreds of employers in South Carolina, hopes to equip staff with telemedicine capabilities and tablet-based billing software as part of its ongoing modernization effort.
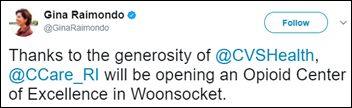
Q2i develops Opioid Addiction Recovery Support software for substance abuse clinics that includes real-time reporting, analytics, and trend analysis via care team portal and patient-facing mobile app.
People

Stanley Crane (Allscripts) joins InteliSys Health as CTO.

Kno2 hires Alan Swenson (Epic) as director of interoperability.
EHRA elects David Heller (Greenway Health) to its executive committee.
Acquisitions, Funding, Business, and Stock

TechCrunch looks at the reasons why singer Lionel Richie (an early investor in Microsoft) chose app-based house call startup Heal as his first foray into startup investing. “I’m going to let the secret out of the bag,” says Richie. “This is my new pastime. I had a choice: Do I play tennis on the weekends or do I call up my tech friends and say what’s new?” Richie is far from the only celebrity investing in technology. Ashton Kutcher, Kobe Bryant, and Ryan Seacrest have all dipped their toes in the tech funding waters.
Telemedicine

ClearHealth Quality Institute creates an online portal for organizations looking to apply for its Telemedicine Accreditation Program. CHQI took the program over from the American Telemedicine Association several months ago.

Rok Mobile will give 1,200 veterans in the greater Los Angeles area free mobile service and telemedicine access next month as part of its new Veterans Helping Veterans program. The company, founded by billionaire John Paul DeJoria (of Paul Mitchell Systems and Patron Tequila fame), hopes to develop the program into a long-term initiative that provides free services to homeless veterans for every two that switch to Rok.
Research and Innovation
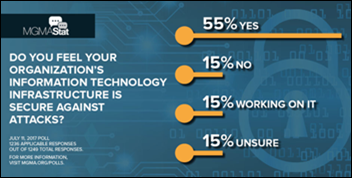
An MGMA survey finds there is still room for improvement when it comes to securing IT infrastructure as part of an organization’s broader cybersecurity strategy. Nearly one-third of the survey’s 1,236 respondents said their organization has faced some type of cyberattack, while 54 percent said they had not and 12 percent were unsure. Backup tapes were the saving grace of those that have been through an attack. “We survived a ransomware attack and didn’t have to pay – used our backup tapes and were fine,” said one provider. “I feel safe, but I also know we are all vulnerable.”
Other
Greenway Health donates EHR software to The Pregnancy Resource Center, a new free clinic run by the nonprofit Community Christian Council. “It’s kind of a mission of Greenway,” says Greenway Health VP of Interoperability Rob Newman. “We started out with the Rapha clinics, which are very similar to this, working with the underprivileged. This just seemed like a good fit.” The center is not far from Greenway’s headquarters in Carrollton, GA.
Sponsor Updates
- EClinicalWorks will exhibit at the 2017 Michigan Primary Care Annual Conference July 24 in Acme, MI.
- Medical Billing Service Review includes AdvancedMD in its list of top five medical billing service companies.
Blog Posts
- The real problem with EHR training isn’t webinars, learning styles, or physician buy-in (Nordic)
- The house call, once upon a time (EClinicalWorks)
- Are you a brilliant woman? We’d like to talk. (Nordic)
- 6 Ways Content as a Service Boosts Your Business (Healthwise)
Contacts
More news: HIStalk, HIStalk Connect.
Get HIStalk Practice updates.
Contact us online.
Become a sponsor.

























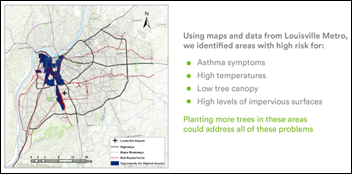

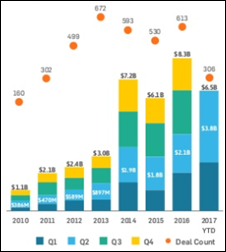





The article about Pediatric Associates in CA has a nugget with a potentially outsized impact: the implication that VFC vaccines…